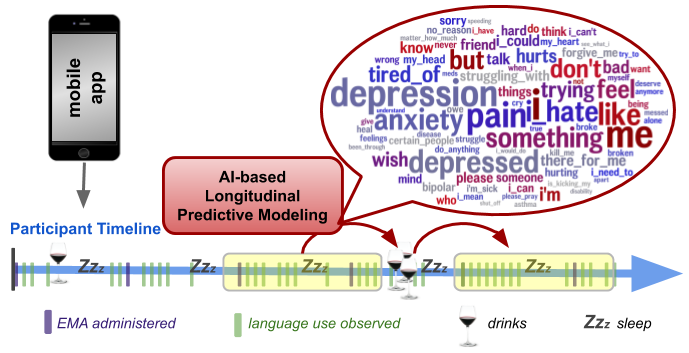
AI Institute Faculty Member Receives $2.5 Million NIH Award for Unique Study
spotlightimage

Spotlight Link
https://ai.stonybrook.edu/about-us/News/AI-Bayesian-Inference-Complex-Systems
Spotlight Type
Electrical and Computer Engineering Professor Talks About the Tools at the Center of AI Applications
The emerging application of artificial intelligence (AI) to a diverse range of fields has positioned it as a valuable research tool. Stony Brook’s Institute for AI-Driven Discovery and Innovation hosts faculty from a wide variety of disciplines who are advancing machine learning research.